As many of you are probably aware, there’s lots of people out to try to defraud you on the ‘net. Its not personal, just a way for them to increase the money they get. I received a spam mail today allegedly from 1&1 IONOS:
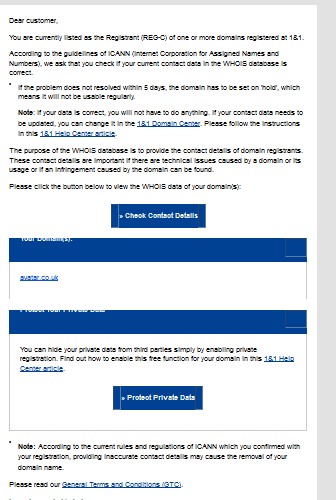
Because Gmail blocked it as spam, I paid it no real attention but I figured I’d take a look as its even got the avatar.co.uk domain there.

So, hovering over the links it pointed to a domain. I checked the domain against whois and surprise! Nothing there.
In the body of the e-mail I see:
| If the problem does not resolved within 5 days, the domain has to be set on ‘hold’, which means it will not be usable regularly. Note: If your data is correct, you will not have to do anything. If your contact data needs to be updated, you can change it in the 1&1 Domain Center. Please follow the instructions in this 1&1 Help Center article. |
This is the classic, “you’ve gotta do something within the time limit, or bad things happen!”. Although in this case, it appears that they’re not too sure what you should do (Both doing nothing AND placing domain on hold within 5 days). Also the grammar of the first paragraph is terrible; the things sent out from a company as big as 1&1 is very unlikely to have these sort of mistakes.
Next for the fun of it, I went to the domain in the “Check Contract Details” (after removing any tracking junk):
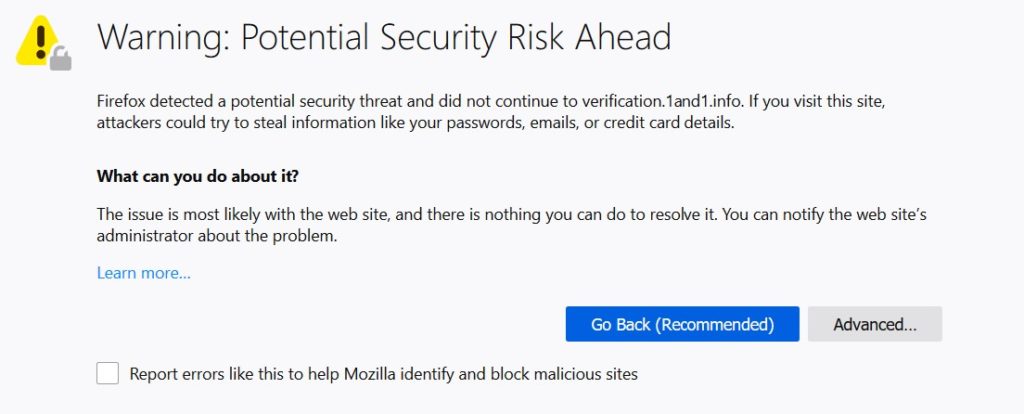
So, if by this point, you continue, you probably deserve any malware that’s on that site.
Also note that they’ve tried to be clever by using https, but couldn’t get the certificate to verify correctly. This is why you need to use the latest version of a browser – its got mechanisms in place to detect this.
For me, this was interesting as I’m guessing they were trying to get me to log onto their copy of the 1&1 account page with my details so they could steal my account. From WHOIS they could tell that 1&1 hosted the site and they sent it to an e-mail contact address from the webpage (which is NOT the one used for my 1&1 login).
Its certainly a better attempt than the ones that show an image email and say “you’ve been hacked pay me bitcoin, please”.
